

Securi-Tay is an information security conference held annually at Abertay University, organised by Abertay University's Ethical Hacking Society. This year's edition will welcome over 350 attendees and marks the tenth annual Securi-Tay, Europe's largest student-run information security conference.
Securi-Tay runs across three separate tracks and welcomes talks from both seasoned professionals and first-time speakers! Additionally, there will be workshops hosted in a separate workshop village throughout the day.
Securi-Tay would not be possible without the support and generosity of our sponsors; attendees will have the opportunity to network with some of our sponsors in the main exhibition space throughout the event.
This year the conference will be run on Friday 4th of March at Abertay University.
Attendees of the event must abide by the AbertayHackers Code of Conduct which can be found here.
Registration will be in the Old College Building. Follow the signs and volunteers to sign in and collect your free swag!
60 mins
Old College Building, Room 1001
A brief welcome and introduction to the conference.
15 mins
All Tracks
This talk is about our history, about the things we got right, and the things we got wrong, to get to here, and what we believe people can do to have a long-lasting positive impact in a problem that – sometimes – feels too big to tackle.
60 mins
All Tracks
Federico is the founder and Chief Executive of Quorum Cyber, a UK cyber security firm enabling customers globally and across industries to confidently operate in a hostile digital landscape.
Federico has 20 years’ experience providing cyber security services across Americas, Europe, and Middle East. He was previously VP Group Head of Security at a Middle East bank; Company Director and Head of Consulting for a cyber security firm in UK; Senior Advisor for several blue chip and FTSE100 companies.
No more alert(1) aims to get pentesters and blue-team security professionals on the same page. After listening to blue-team and non technical staff (everyone from seasoned security professionals to non technical project managers), this talk aims to bridge the gap between the two arms of security by showing the different ways proof of concepts can be gathered. A deep dive into exploiting XSS and a light touch on some of the other vulnerabilities, combined with all the best ways to demonstrate how to show exploitability to clients, means that whether you're a hardened CTL, a new product manager without technical knowledge, or entry level in any discipline, you should walk away having learned something new.
60 mins
Track 1
Professionally, I look after the Service Desk and Service Development at Pentest People (pentestpeople.com), am the volunteer IT Director at Trust Leeds (trustleeds.org.uk) and develop the various service offerings at DarkInvader (darkinvader.io). Personally, I love coding tools to make pentesters lives easier, with a little bit of martial arts on the side!
Whether you're a company's first security hire or you're on your first steps to becoming a security manager, it can be tough to know what to do first.
This talk covers everything you need to get started, from technical skills and tools you can deploy through to the do's and don'ts of dealing with other teams within the business to make sure you make progress and can build a valuable security program.
60 mins
Track 2
Jamie is Head of Security at Rasa and has previously worked as a security engineering lead at Fortinet and ZoneFox. He works on bringing usable security to businesses and making sure that security isn't seen as The Team Who Says No.
Social engineers use several techniques to bluff, charm threaten or deceive their way into getting someone to commit an act that may or may not be in their best interests. Over the past year I have been doing research into social engineering, the psychology behind influence and how malicious actors combine the two to manipulate and influence people into undertaking actions that are not in their best interests. This presentation will show the six pillars of influence and how they can transpire to trick people like you or me.
30 mins
Track 3
Connor currently works as an Analyst at Pa Consulting, working on various cloud security projects. He graduated from Abertay University in 2020, and has a particular interest in Social Engineering and the psychology behind people.
ontainers are only increasing in popularity, with Docker being almost synonymous with the term but one thing a lot of us don't consider is the security. Just because they are inside a container does not mean they are fully isolated or invulnerable to attack. My talk is going to discuss a brief history of containers, how they work and why do we use them. Then going to talk about some common vulnerabilities, famous CVEs and a hacker group or two you may want to look out for! Finally what are some ways to secure your container from super simple solutions like namespacing to more complicated and involved methods such as creating custom AppArmor profiles for your container applications.
30 mins
Track 3
An Abertay alumni who is currently working as a cyber security analyst, Mairi has a love/hate relationship with containers. Where she loves breaking out of them and hates having to spell Kubernetes. Hobbies wise Mairi spends her free time taking photos of her cat, watching anime and waiting in Final Fantasy raid queues.
This talk revolves around the open source reverse engineering toolkit Radare2 (r2) - which is written in C and has been in development since 2006. Radare2 is an advanced suite of tools & features for working with binaries on many platforms and architectures. The tools also come with language bindings for many popular languages allowing for easy plugin/tool development.
During this talk, we'll blitz over 60 interesting features or Easter eggs available in Radare2, in 60 minutes. The aim is to pique your interest in r2 by showing you features that you can use to make your life easier, whether you're doing DevSecOps, reversing code, or mobile app pentesting.
Hold tight, we're going for a bit of a 0x72 0x69 0x64 0x65.
60 mins
Track 1
Grant is an Abertay Ethical Hacking alumni and has been in the industry for over 8 years. Grant is currently a Principal Consultant at Synopsys and specialises in mobile security - holding strong skills in reverse engineering, threat modelling, pentesting, code review, and more.
Grant has contributed to common open source tooling such as Frida & Radare2 and has presented frequently at conferences on various AppSec topics.
Not all talks are Red/Blue/Purple, some are learning opportunities for all. HoneyPoC opened the eyes of many folks and why is it important to be careful about the Proof Of Concepts(POC) that you download/review. What started off as a minor troll turned into an integrated research project, the talk will embark on knowledge about steps taken to uncover insider threats via passive analysis and identification of internal hosts.
This was a particularly "amusing" troll because the sort of people who keep up with CVEs and look for proof-of-concept exploits should really know better than to run random code they just got off GitHub without checking what it does.
60 mins
Track 2
Andy is a seasoned offensive security professional who specialises in red and purple teaming with a focus on obscure insider threat attacks. He is a hacker at heart and a keen supporter of the wider community with blog posts, talks and podcasts. Most known for his book LTR101 and HoneyPoC, a troll that became a research project.
Video game cheating is an interesting dilemma faced by game development companies. With cheats being originally built into games, being unlocked with a code. To China arresting cheat makers for games.
The current solution is software used to detect the presence of cheating done by the user of the device, known as "Anti-Cheat". Which is like running anti-virus on a malware creators’ computer.
This talk will discuss about what is anti-cheat, its history, the present, the good, the bad and the silly.
30 mins
Track 3
I'm a Abertay ethical hacking year 3 student, and I like computers (Big surprise). I've done a talk before at the Abertay Ethical hacking society (And at the time of writing am preparing to do another talk).
1 - Brief Overview of Talk Structure
2 - Career Change to Cyber - My reasons behind leaving and teaching and why I am pursuing Cybersecurity.
3 - Why teachers should consider retraining to cyber and why cyber should consider training teachers (many skillet crossovers I will expand on)
4 - Reflection on experiences of first year so far and challenges other career shifter may face if retraining to cyber.
5 - Questions/Suggestions/Advice from audience
30 mins
Track 3
Ewan Taylor is a 1st year Cybersecurity student, former teacher and music graduate, now seeking to build a new career in the exciting world of Cybersecurity.
In this Lego cyber resilience tabletop exercise, your team has been tasked with the mission of managing the security of a newly acquired power plant. You will be given a small budget to implement a range of different defensive cyber options.
Your team of up to 8 players will be given 60 minutes to use your decision-making skills to determine the best course of action for the organisation.
Will you keep the plant running?
NOTE: You must sign up for the session beforehand. Visit the Waterstons sponsor stand to sign up. Either create your own team (max 8 players) or individually sign up and we will assign you a team.
60 mins
Workshops
Waterstons are an NCSC approved Cyber Consultancy with over 25 years of helping our clients to protect their critical data and reputation. Our mission is to become a trusted security partner to our clients, continually protecting their organisation from the evolving cyber threat landscape. Waterstons contain a range of experts in all areas of information security, from the Cyber Resilience Team to our 24 x 7 Security Operation Centre (SOC).
Supply chain attacks are higher profile than ever, and Continuous Integration and Continuous Development (CI/CD) pipelines are rapidly forming the basis of modern software development and DevSecOps workflows. These pipelines grant developers flexibility to perform automated testing regularly during development, and can aid in reducing the number of steps required to get code from a keyboard to a development environment. While this is convenient for developers, with great convenience comes great attack surface. This presentation will provide an introduction into CI/CD pipelines, then discuss some of the ways we have compromised customer environments using a pipeline or code repository as a starting point. The presentation will draw common attack paths and escalation vectors, and hopefully provide some useful guidance on how to lock down your own environments and reduce the blast radius of a compromised pipeline.
60 mins
Track 1
Iain is the containerisation and orchestration practice lead at NCC Group. He enjoys playing with new technologies, and if he's not hacking a Kubernetes cluster or attacking a build pipeline he can probably be found writing new home automations to annoy his family.
Nudes, Dirties, Pics, whatever you call them, you’ve probably sent them or know someone who has. But how can we protect ourselves and our opsec when we’re sexting, producing sexual content of ourselves or even watching and buying sexual content online?
This talk will discuss how we can protect our physical bits online, how to practice safe sexting properly, how we can learn opsec from sex workers and looking into the weird, wonderful and sometimes scary world of sex online.
This talk has been delivered before, but has been updated to include new content about sex toys, porn consumption and how it's changed over the years, as well as how the pandemic affected sex online. CONTENT WARNING - There will be sensitive content discussed in this talk such as sexual violence, domestic abuse and suicide
60 mins
Track 2
Tia is a fourth year ethical hacking student at Abertay University. She has delivered various workshops and talks at conferences and societies around the country. These talks and workshops vary from social engineering, offensive security and most recently discussing how to practice safe sex online.
This talk is designed for people looking to break into computer security, and specifically the vulnerability research field. During this talk we'll break down training techniques, principles, and approaches that we've used to help develop the next generation of vulnerability researchers and how those same techniques can be applied to your own training. This will include:
- Example training plans
- How to manage your own training if your organisation doesn't provide it
- How to structure your training
- How to make your training more than a tick box excersise
- How to get the most from your training
- Lesson's learnt, and what didn't work for us
- A walkthrough of how we train our vulnerability researchers
30 mins
Track 3
James Stevenson is a vulnerability researcher, public speaker, and published author. James has been in the computer security field for around 5 years and currently works for the vulnerability research company Interrupt Labs. At IL James, with others, have developed a training platform from the ground up - designed to bring those new to computer security to the level of specialised vulnerability researchers.
From libncom.so to Jynx, Azazel to "libcurl", userland Linux rootkits have been a growing, but often ignored, part of the Linux malware ecosystem for over a decade now.
Despite crippling architectural flaws, this evolutionary dead-end of sorts in Linux malware continues somehow to thrive due to the relative ease of development, deployment, and reliability when compared to kernel based rootkits. Somehow, they even evade modern, expensive EDR products.
This talk will be a brief primer on this category of rootkits. Where it began, where it is, and where you can take it next.
30 mins
Track 3
Darren is a security researcher/consultant based on a small, damp rock In the Atlantic with a special fondness for Linux malware.
In this Lego cyber resilience tabletop exercise, your team has been tasked with the mission of managing the security of a newly acquired power plant. You will be given a small budget to implement a range of different defensive cyber options.
Your team of up to 8 players will be given 60 minutes to use your decision-making skills to determine the best course of action for the organisation.
Will you keep the plant running?
NOTE: You must sign up for the session beforehand. Visit the Waterstons sponsor stand to sign up. Either create your own team (max 8 players) or individually sign up and we will assign you a team.
60 mins
Workshops
Waterstons are an NCSC approved Cyber Consultancy with over 25 years of helping our clients to protect their critical data and reputation. Our mission is to become a trusted security partner to our clients, continually protecting their organisation from the evolving cyber threat landscape. Waterstons contain a range of experts in all areas of information security, from the Cyber Resilience Team to our 24 x 7 Security Operation Centre (SOC).
This talk will be based around my experience as a Security Analyst. My focus will be around Microsoft products: Azure Sentinel and Log Analytics and how investigations can be performed with the use of Kusto Query Language (KQL). The talk will give a bit of an insight into what the role of a security analyst means and what are the benefits of this path.
60 mins
Track 1
I am a graduate apprentice studying GA Cyber Security at Edinburgh Napier University. I also work as a Security Analyst at Quorum Cyber. My journey with Cybersec started over 2 years ago when I joined the graduate apprentice program coming from an administration/customer service background. As part of my job I mainly work with Microsoft products like Azure Sentinel and Defender platforms to investigate security alerts. I’m also involved in security engineering, incident response and customer engagement, which allows me to gain a better understanding of cybersecurity industry as a whole. In my ‘free’ time between work and uni, I’m a mum of two and strive to engage with the infosec community by attending conferences and mentoring.
Over the past year I have been doing research into OSINT as part of a research proposal.
I will present an in-depth view on how I am building a social scoring system by compiling detailed profiles on people existing in the UK (Specifically England).
This talk focusses on the social aspect of having an online presence, and the dangers associated. It presents ethical questions regarding data governance and the right to privacy.
By the end of this talk you should have a detailed idea on how Governments, Adversaries and other organisations are able to build up an entire profile of your personal life, and how to best defend against it.
60 mins
Track 2
Dylan Wheeler is an ex-blackhat hacker known for his involvement in the Xbox Underground hacking group (featured by WIRED US and Darknet Diaries). Dylan currently resides in London and has been a major advocate for responsible disclosure in recent years, working largely within both the financial and entertainment sectors. Dylan takes an unusual and often eccentric approach towards the information security field and in 2019 was rumoured to be assaulted at the ICE London conference by a vendor for a security disclosure gone awry.
During an IR case, there are many well-known sources of evidence which can be used for triage or in-depth investigation. Because these artifacts are familiar to investigators, mature tooling and analysis capabilities are available. However, adversaries have the same level of understanding and can use it to cover their tracks. While many e-crime groups just don’t care, other more advanced actors have created tooling to automate anti forensics. For example, the uncategorised threat group, tracked by FireEye as UNC1945, utilizes an ELF executable called LOGBLEACH which deletes log entries in a selection of log files such as syslog and auth.log. In lieu of the usual sources, investigators must rely on more obscure artifacts to fill in the blanks and solve the case.
This talk will outline the threat landscape and drill down into the process of identifying novel forensic artifacts using the example of the wget-hsts file.
30 mins
Track 3
Joe is a Security Researcher and Incident Responder, currently studying Cybersecurity & Forensics. He has previously worked as a Site Reliability Engineer and enjoys programming in his spare time. AFK, Joe is into fitness, travel and photography.
This talk will explore the understudied technology of QR codes. Most people will know what a QR code is, and have likely scanned many throughout their life. Very few people know how the technology works, nor have considered the use of QR codes for alternative uses. With the newly increased usage and acceptance of QR codes caused by covid track and trace, more people will be willing to and expecting to scan a QR code on their way into a building. This increased prevalence further escalates the probability of QR codes being used for a more modern version of phishing.
30 mins
Track 3
4th-year ethical hacker, I've attended 3 Securi-Tays so far and many other conferences. I want to be able to speak at our home conference to give back for all the good conferences that have been run in past years.
A workshop to show people how to map out there active directory and what attacks can be used to compromise AD. Workshop will include a vulnerable AD to run tooling against and demos of how to attack these findings and how to fix them.
120 mins
Workshops
Derek is a Principal Security Consultant at NCC Group with over 10 years of experience in cyber security. His expertise in penetration testing and consultancy spans most technologies, from Windows security to telephony. He has worked with a variety of clients across all sectors, including many FTSE 100 and Forbes 2000 companies.
Derek holds a degree in Internet Communications and Networks and has been a CREST Certified Tester for over 6 years. He is an expert in general security consultancy, with additional specialisms in infrastructure, Azure, Active Directory and scenario-based penetration testing.
Derek has previously featured as a keynote speaker at Securi-Tay V, presenting on iOS forensics.
A look at how attempted Operational Security (OPSEC) failed in practice for a group of alleged January 6th Capitol attackers.
This talk analyses the steps taken by the group to organise, protect their identities and communications.
60 mins
Track 1
Former AbertayHackers Vice Gaffer. Purveyor of macOS security & rum.
War Studies postgrad Terrorism, Radicalisation & British intelligence. Security Engineer.
Talk will cover entry-level industry certifications, ways to demonstrate an active interest in offensive security and what to expect daily as a penetration tester in the 9 to 5 job. Additionally, coverage of the most common types of testing engagements experienced as an offensive security professional.
60 mins
Track 2
Mark is an experienced Penetration Tester who graduated from Abertay in 2016. Since then, Mark has went on to engage with clients worldwide to help them improve their security maturity and improve their defences against attackers. Outside of work, Mark hacks his way around the golf course.
When considering defending and protecting web applications, rarely do we speak about what the web applications themselves can actively do when under attack. Built-in detection and response capabilities can be a highly effective and underutilized method to mitigate attacks and to act as a canary for malicious activity.
In this talk, I'm going to introduce the concept of application intrusion detection and highlight the techniques available to make web applications attack-aware. Furthermore, I will also illustrate ongoing research on how developers can take advantage of their frameworks and language-level mechanisms to get started.
30 mins
Track 3
Hey there! My name is Tolga and I'm one of the PhD candidates in Cybersecurity here at the Abertay University. In my research, I'm investigating the integration of attack-awareness capabilities in web applications, a topic where also two of my favourite interests come together - development & security. Before I re-joined Abertay for my academic journey, I have worked as a web application engineer for a Startup in the lovely region of Allgäu (Germany), where I'm currently based.
Twitter: @tolgauedev
Homepage: https://tolgadevsec.github.io
The Secureworks Counter Threat Unit constantly analyses threat data across our worldwide customer base and actively monitors the cyber threat landscape to provide a globalised view of emerging threats, zero-day vulnerabilities, and the evolving tactics and techniques of advanced threat actors. This session will provide the latest intelligence on the threat landscape, considering the criminal threat from ransomware as well as trends from hostile state actors. We will also cover practical measures your security team can use to keep you protected and how Secureworks can help your organisation accelerate threat detection and response
30 mins
Track 3
Don Smith leads the Secureworks Counter Threat Unit’s™ Cyber Intelligence Cell (CTU-CIC), a global team of experienced threat analysts who deliver actionable and timely intelligence products on the threats most relevant to Secureworks clients. Based in the UK, Don also leads the Secureworks CTU research team in EMEA.
Don joined Secureworks in 2005 and his enthusiasm and threat expertise means that he regularly represents the company and their more than 20 years of industry-leading threat intelligence at industry events. With more than two decades of experience in the IT industry, he was previously responsible for security architecture and operations for a multi-billion enterprise and took a lead role in successfully integrating 14 acquisitions. Don is a recognized subject-matter expert in many areas
You’ve found an issue. What should be done about it? Sometimes finding the issue is the precursor to the hard part - fixing the defect. Oftentimes, as security professionals, we don’t think twice about the true scale and impact of what appears to be a slam dunk fix. We use some examples to illustrate how fixes go wrong - usually due to a chain reaction of unanticipated and unintended consequences, or because the design tradeoffs were not considered. The goal of the talk is to motivate attendees to think more deeply about the problem space before proposing a (security) solution.
60 mins
All Tracks
Andrew Lee-Thorp is an occasional speaker, trainer and security jack of all trades who currently works as a Principal Consultant for Synopsys Software Integrity Group where he engages in teaching, threat modelling, pen-testing and bug hunting. Andrew has been in the security trade long enough to experience deja vu every time a new bug comes out. He has lived two previous lives as a software developer and as a research scientist which means he has six lives still to go.
A few words to conclude the day and thank everyone who made it possible
15 mins
All Tracks
Sponsored by F-Secure, join us for a few drinks and lots of awesome chat!
???
The Barrelman
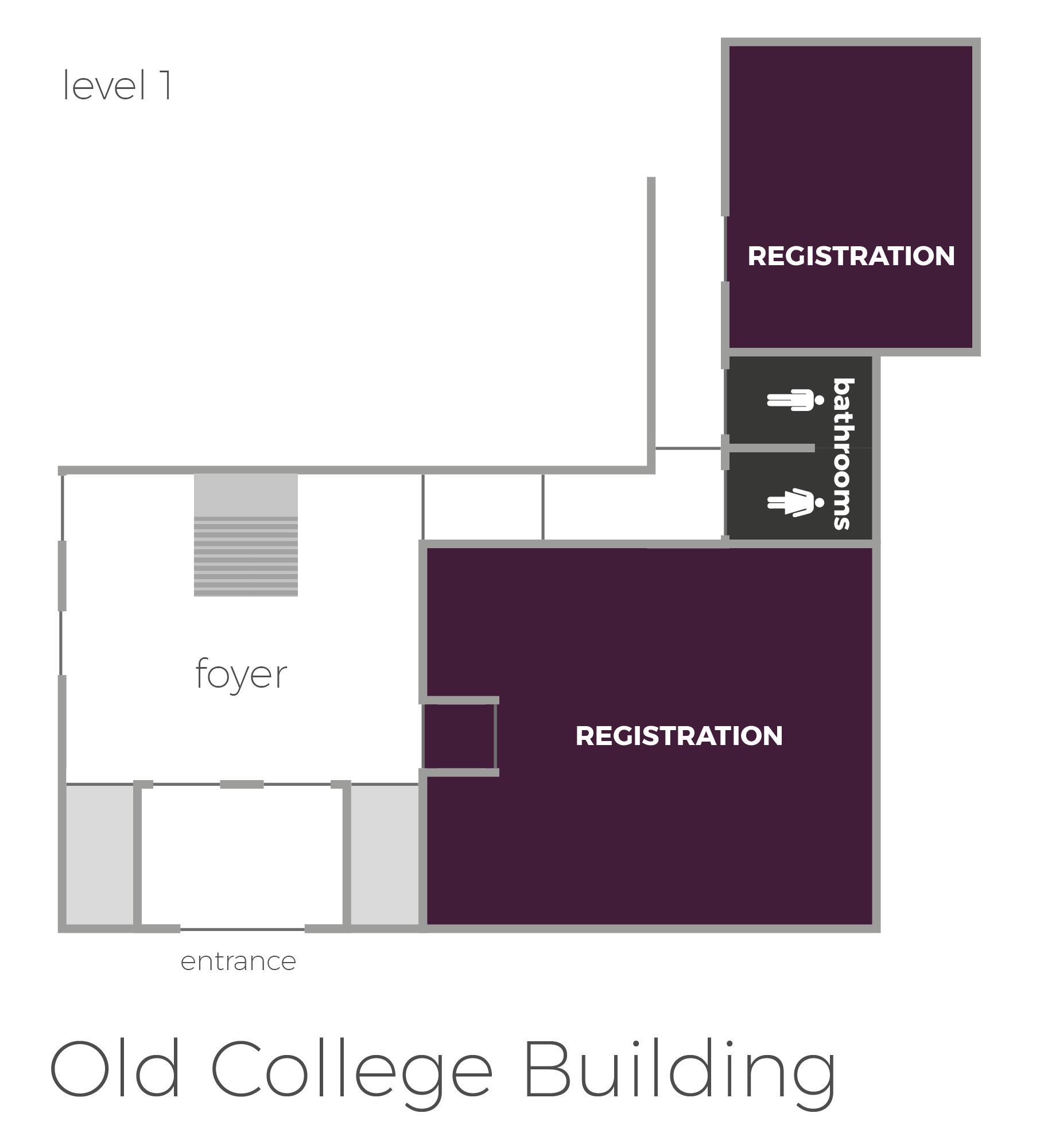
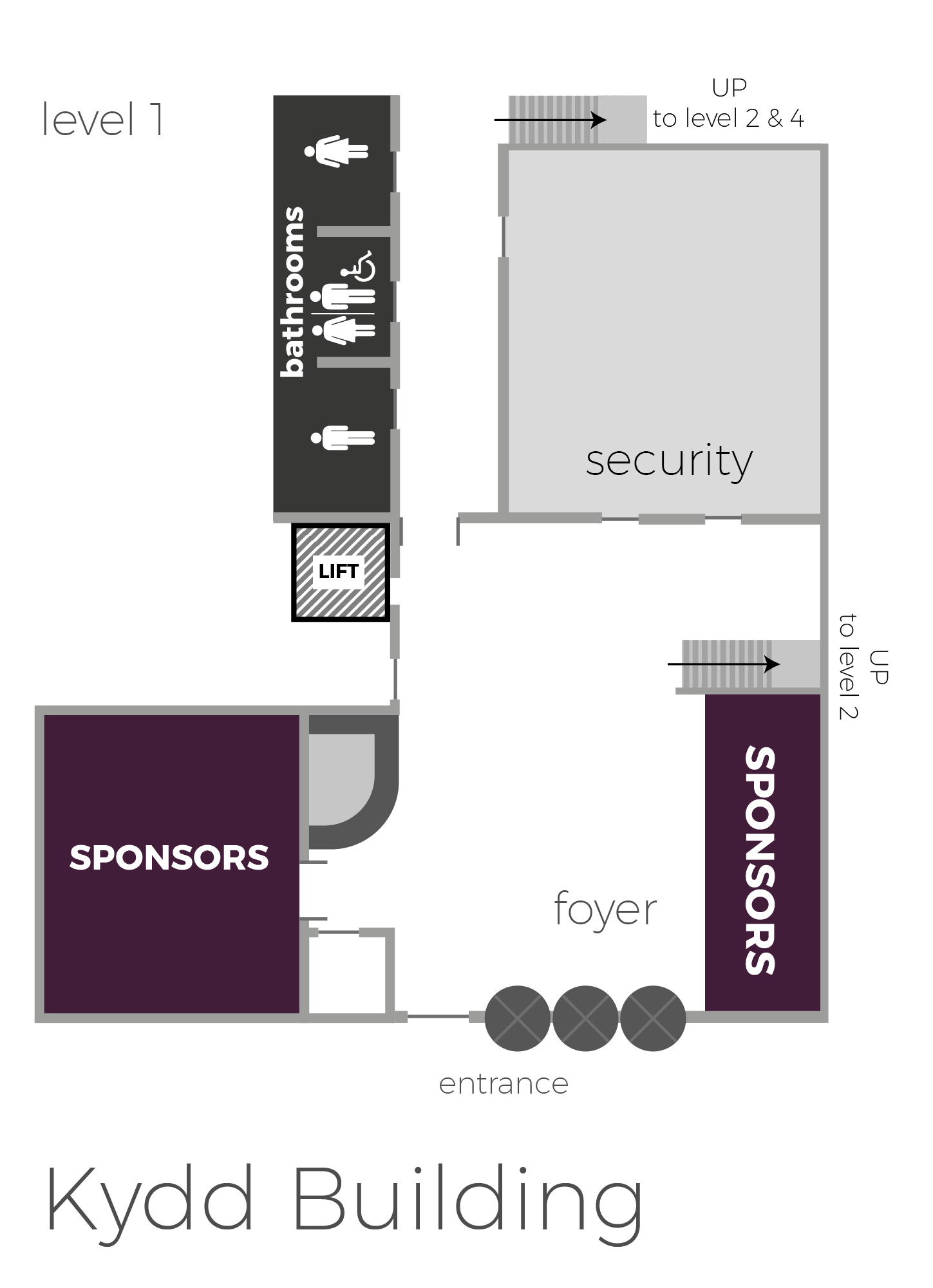
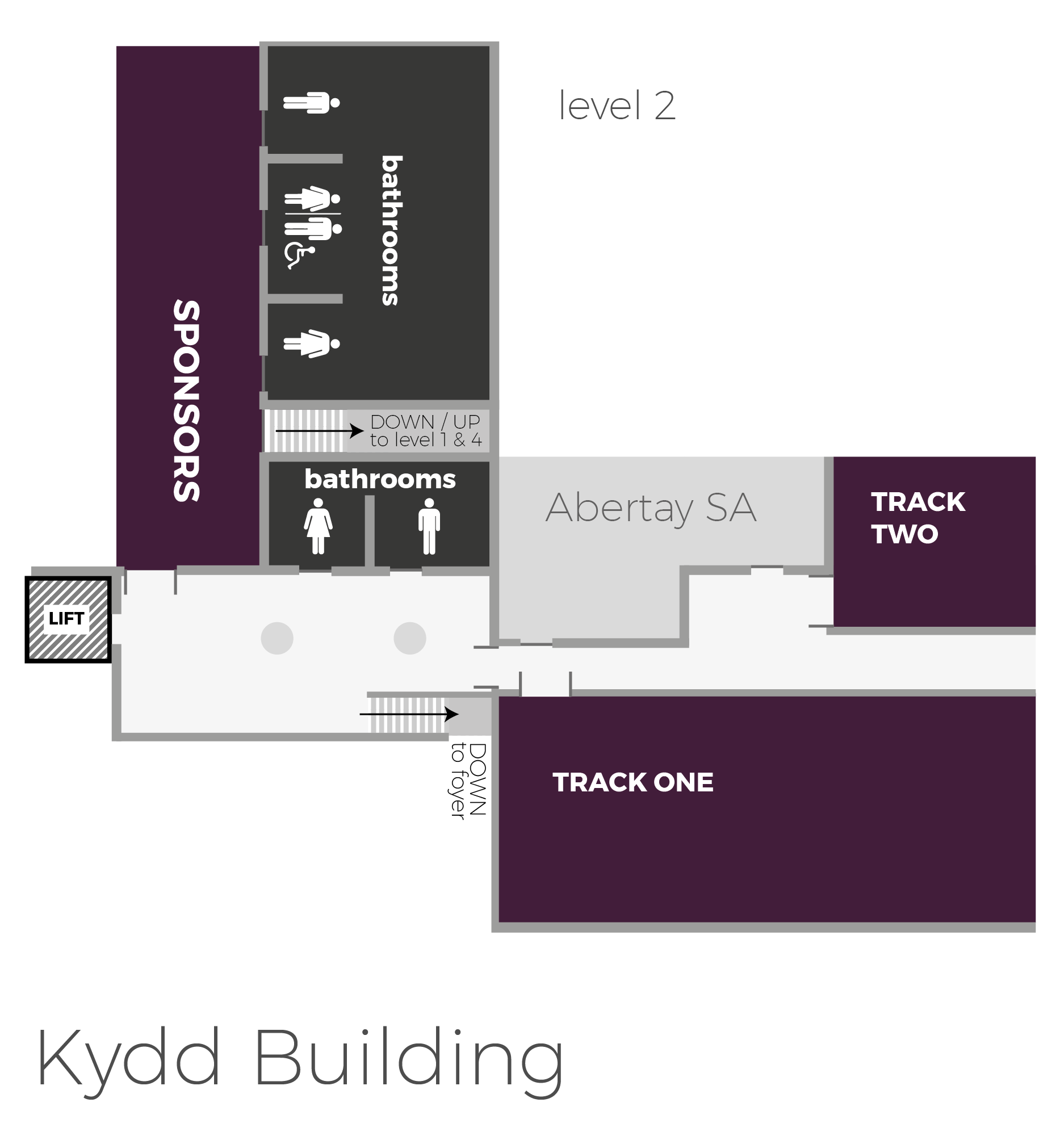
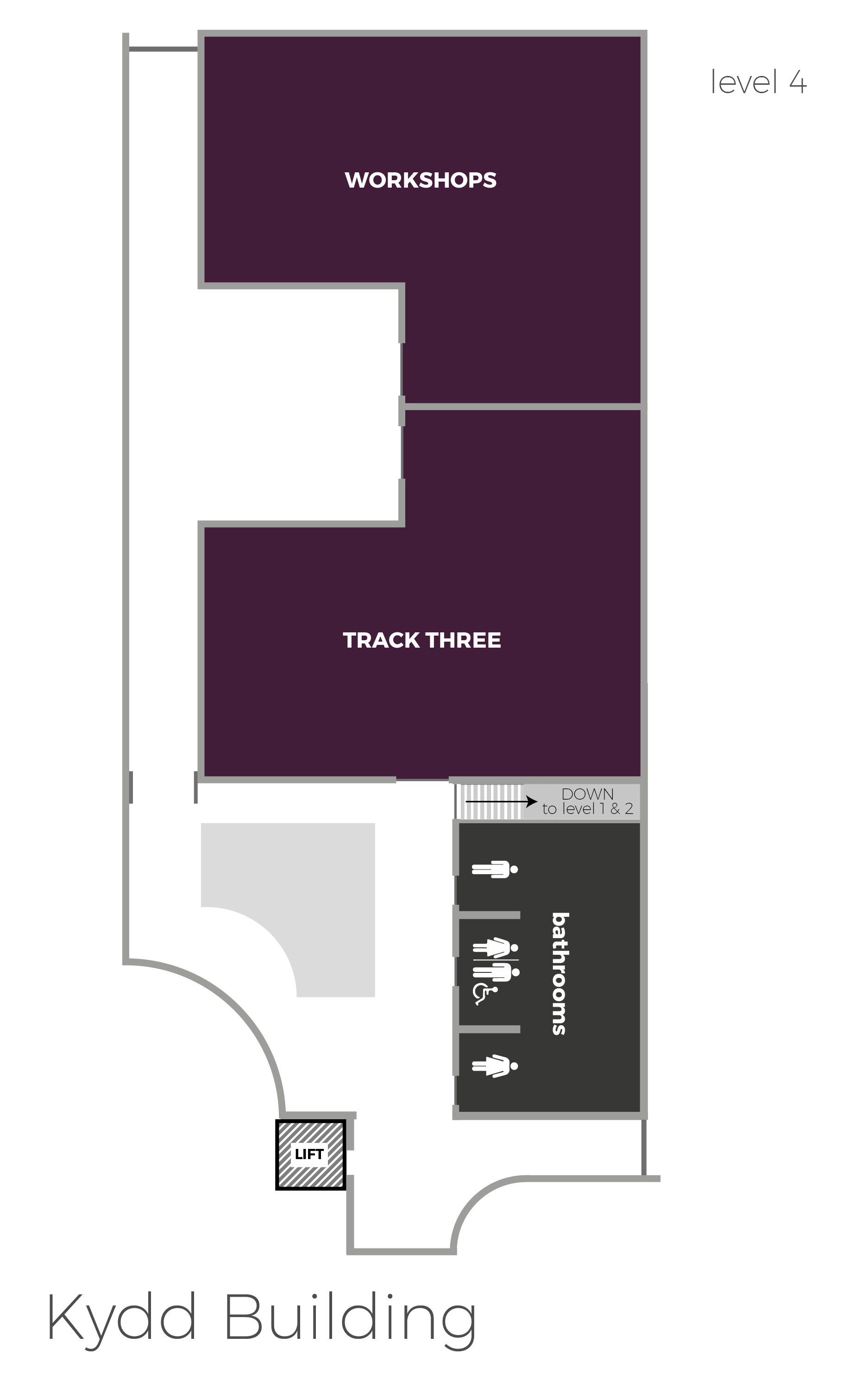

The University's address is Bell Street, Dundee, Scotland, DD1 1HG.
The closest train station is Dundee Station.
The closest airports are Dundee Airport and Edinburgh Airport.
Note: Bell Street is currently being reconstructed and is not viable for parking. If you are driving, the closest parking is the multi-story Bell Street Carpark